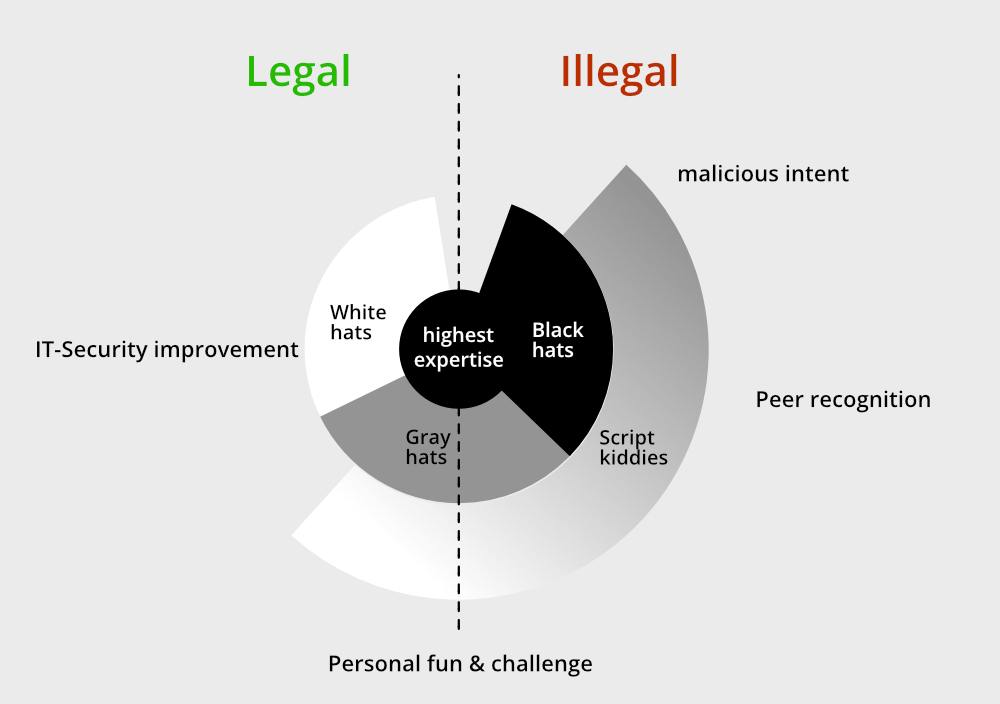
White Hat vs Black Hat vs Grey Hat | Types Of Hackers Explained | Ethical Hacking | Simplilearn - YouTube
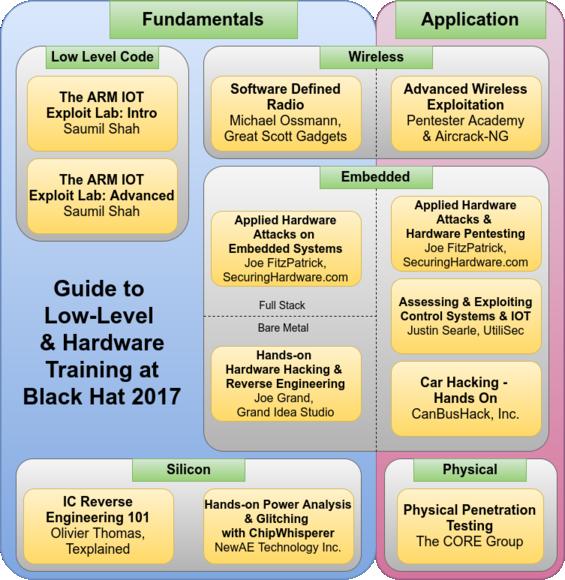
Python Hacker Bootcamp - Zero to Hero • Black Hat • Accredible • Certificates, Badges and Blockchain

Black Hat Python: Python Programming for Hackers and Pentesters: Seitz, Justin: 0884841511358: Amazon.com: Books














![What is Ethical Hacking? A Comprehensive Guide [Updated] What is Ethical Hacking? A Comprehensive Guide [Updated]](https://www.simplilearn.com/ice9/free_resources_article_thumb/ethical_hacking_infographic.jpg)